Introduction
The significance of mobile security in the current digital environment cannot be emphasized enough. Since mobile phones are being used more and more for both personal and professional purposes, it is essential to comprehend how mobile security operates in order to safeguard our private data from harmful attacks. An overview of mobile security, threats to mobile security, fundamentals of mobile security, how mobile security operates, tools and technologies, the role of AI and machine learning in mobile security, employee best practices, regulatory and compliance aspects, emerging trends in mobile security, challenges in mobile security, ways to improve your mobile security, and the future of mobile security will all be covered in this article.
Understanding Mobile Security
The methods, tools, and processes used to secure mobile devices from illegal access, data breaches, and other online dangers are together referred to as mobile security. Maintaining system integrity, protecting user privacy, and maintaining data confidentiality are its fundamental responsibilities. Mobile security is a digital protector against changing threats, no matter whether you’re a single user or a company managing dozens of devices.
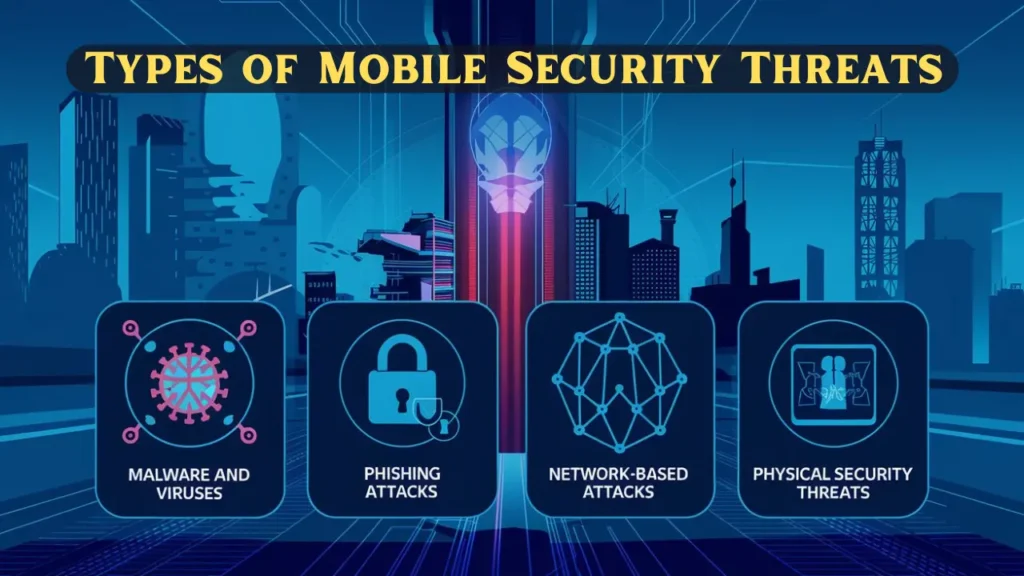
Types of Mobile Security Threats
- Malware and Viruses
Malware like ransomware and spyware can compromise mobile data and applications. A single malicious app download can result in stolen credentials or encrypted files. - Phishing Attacks
Phishing via emails, messages, or apps remains a top threat, tricking users into sharing sensitive details such as passwords and credit card numbers. - Network-Based Attacks
Using unsecured public Wi-Fi networks exposes mobile devices to man-in-the-middle attacks, where hackers intercept communications to steal data. - Physical Security Threats
Lost or stolen devices can lead to unauthorized access to personal or corporate information, highlighting the need for secure lock screens and remote wipe capabilities.
Core Principles of Mobile Security
Effective mobile security strategies revolve around three core principles:
- Confidentiality: Protecting sensitive data from unauthorized access.
- Integrity: Ensuring data remains unaltered and trustworthy.
- Availability: Guaranteeing authorized users can access the information they need. In addition, authentication mechanisms like biometrics and passwords form the foundation of secure access control.
To learn more about core principles, click here
How Does Mobile Security Works
- Device-Level Security Measures
- Encryption: Mobile devices encrypt data to prevent unauthorized access, even if the device is compromised.
- Biometrics: Technologies like fingerprint scans and facial recognition provide robust, user-friendly authentication methods.
- Application Security Measures
- Developers employ secure coding practices to minimize vulnerabilities in mobile apps.
- Users should review and limit app permissions to prevent unnecessary data access.
- Network-Level Security Measures
- Virtual Private Networks (VPNs): VPNs encrypt internet traffic, securing communications over untrusted networks.
- Secure Wi-Fi Usage: Avoiding public Wi-Fi or connecting through secure networks prevents many cyber threats.

Mobile Security in Action
Imagine losing your phone at a crowded event. With robust mobile security, encrypted data, and remote wipe functionality, the chances of sensitive information falling into the wrong hands are drastically reduced. Conversely, a lack of security could lead to identity theft or significant data breaches.
Tools and Technologies in Mobile Security
Mobile security tools include antivirus software, mobile device management (MDM) systems, and firewalls. These technologies work together to monitor, detect, and respond to potential threats, ensuring comprehensive protection.
Role of AI and Machine Learning in Mobile Security
Advanced AI algorithms analyze vast amounts of data to identify anomalies, predict threats, and automatically deploy countermeasures. This proactive approach enhances mobile security by adapting to emerging threats in real-time.
Mobile Security in the Workplace
As businesses embrace BYOD policies, ensuring device security becomes a shared responsibility. Organizations implement security policies, such as mandatory software updates and restricted app downloads, to mitigate risks and safeguard sensitive data.
Regulatory and Compliance Aspects
Laws like GDPR emphasize the protection of personal data on mobile devices. Enterprises must comply with these regulations to avoid hefty fines and reputational damage.
Emerging Trends in Mobile Security
The advent of 5G promises faster connectivity but also introduces new security challenges. Blockchain and Zero Trust architecture are emerging as promising solutions to bolster security in increasingly connected environments.
Challenges in Mobile Security
Maintaining mobile security is a continuous battle against rapidly evolving threats. Balancing user convenience with security and allocating resources effectively remain significant challenges, especially for smaller organizations.
How to Enhance Your Mobile Security
- Use strong passwords and enable two-factor authentication.
- Regularly update your device’s software.
- Avoid connecting to public Wi-Fi without a VPN.
The Future of Mobile Security
Mobile security will only grow in importance as the world becomes more interconnected. Emerging technologies like AI and 5G will play a pivotal role in shaping the future of secure mobile environments.
Conclusion
Mobile security is more than a technological necessity—it’s a critical component of modern digital life. By understanding its principles, employing robust tools, and adopting best practices, users can protect their devices and data against ever-evolving threats.

